Linux SSH servers, specifically, stand out to cyberattackers. Their capacity to supply distant command-line entry positions them as important conduits for controlling and managing server operations.
Consequently, this distant entry designates them as prized entry factors for these intent on exploiting or compromising vital companies.
Server directors can run updates, apply patches, and use fewer customary ports to discourage hackers, however how will you inform if the enemy is on the gates?
Spot the Indicators of a Hack
Many hacks aren’t refined. Most end result from automated assaults by botnets or “script kiddies” wielding pre-existing malicious code.
These assaults, starting from denial-of-service (DoS) assaults to the commandeering of servers for spam distribution or cryptocurrency mining, underline the range of cyberthreats.
Such actions reveal a mix of intricate schemes and the opportunistic abuse of well-known vulnerabilities that considerably tax system assets.
Indicators of compromise, akin to delayed emails, disrupted streaming, or a noticeable slowdown of your server, are indicators of potential unauthorized entry. Acknowledging these indicators early on empowers you to behave swiftly.
Happily, there are simple measures you possibly can undertake to confirm the safety of your server. The next are steps to assist guarantee your server’s integrity stays intact.
Step 1. Verify Energetic Logins
If a foul actor has hacked your server, they may nonetheless be signed in. The best approach to test if so is to hook up with your Linux server through SSH and run:
w
This straightforward one-letter command shows different linked customers and their login occasions. Ideally, this may present that there aren’t any different logged-in customers apart from your self (as pictured).
In the event you run the “w” command, you possibly can see the IP deal with of different linked customers through the ‘FROM’ subject. You should utilize the whois command to find out the place the IP was initially registered:
whois 8.8.8.8
You too can view details about logged-in customers and any energetic processes they’re working with:
who -u
Step 2. Verify Earlier Logins
If no unknown customers are at the moment logged in to the server, you also needs to test your server’s login historical past. The best manner to do that is by working:
final
The output from this shell command will show the username, IP deal with, and login occasions of earlier customers.
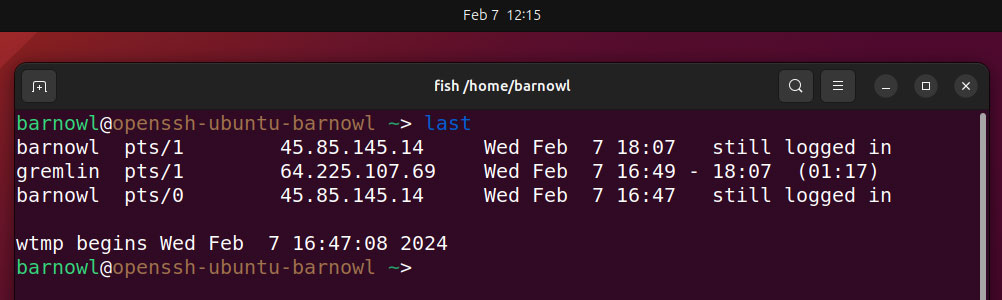
In the event you don’t acknowledge a consumer, as with “gremlin” within the above picture, you possibly can rerun the command with their username to view solely their login historical past, e.g.:
final gremlin
You too can use the ‘whois’ command on the login IP deal with as soon as once more to attempt to hint their location.
If the consumer is unauthorized, you possibly can terminate their SSH session and any processes related to their username utilizing pkill, as an example:
sudo pkill -U gremlin
When working the final command, you’ll discover the ultimate line of output refers to ‘wtmp’, e.g.:
“wtmp begins Wed Feb 7 16:47:08 2024”
Ensure to pay shut consideration to the date and time. If it’s latest, a hacker could have deleted /var/log/wtmp, which shops latest login makes an attempt, to cowl their tracks.
Step 3. Verify Earlier Instructions
In the event you uncover unrecognized customers, you need to test to see which instructions have been run. This listing is saved in ~/.bash_history, which you’ll be able to view from Terminal by working:
cat ~/.bash_history
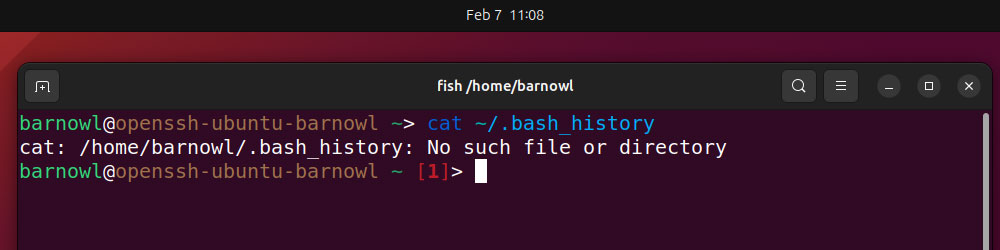
Often, you’ll see a protracted listing of instructions right here. Hold your eyes peeled for frequent instructions akin to set up, curl, or wget, which can be utilized to obtain and set up malicious software program.
If Terminal tells you there’s no such file or listing, a hacker could have deleted the listing to cover traces of instructions they’ve run.
Step 4. Verify the Most Intensive Processes
As we’ve realized, hackers who break into servers will typically start system-intensive processes, akin to putting in packages designed to mine cryptocurrency.
You’ll be able to test if so utilizing the high command: a built-in Linux utility that gives a real-time, dynamic view of the system’s efficiency.
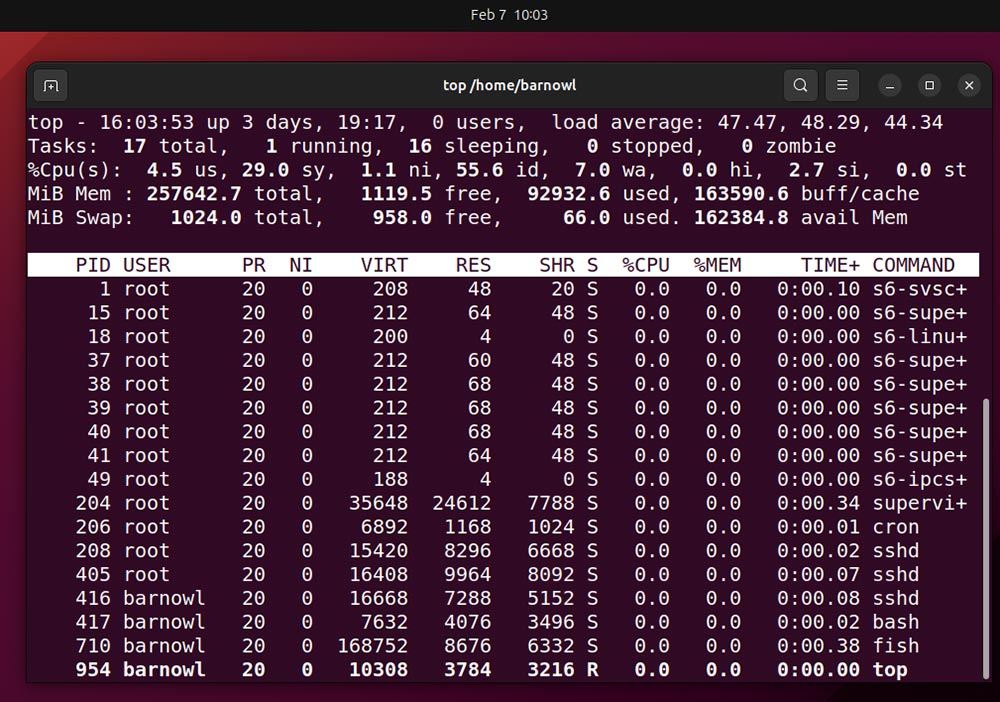
The data right here can appear overwhelming, so first, merely deal with the “command” column, which lists the names of energetic processes. In the event you see any you don’t acknowledge, notice its PID (course of ID). While you’re performed, use Ctrl + C to exit.
The primary and easiest check you possibly can run on an unrecognized course of is to run its title by means of a search engine. As an example, googling “fish linux course of” reveals that the method listed within the picture above is only a user-friendly command line shell.
You can also uncover which recordsdata have been accessed by a selected course of utilizing lsof together with the method ID, as an example:
lsof -p 772
Step 5. Verify All System Processes
If the hacker is sensible, they’ll guarantee that their put in packages don’t hog too many system assets to try to keep underneath the radar. Consequently, the processes they provoke won’t seem within the listing generated by the high command. To double-check all working processes, use:
ps auxf
This command organizes working processes logically. The columns listed below are self-explanatory. As soon as once more, the method ID (PID) and CPU and reminiscence utilization are listed as a proportion of the system general.
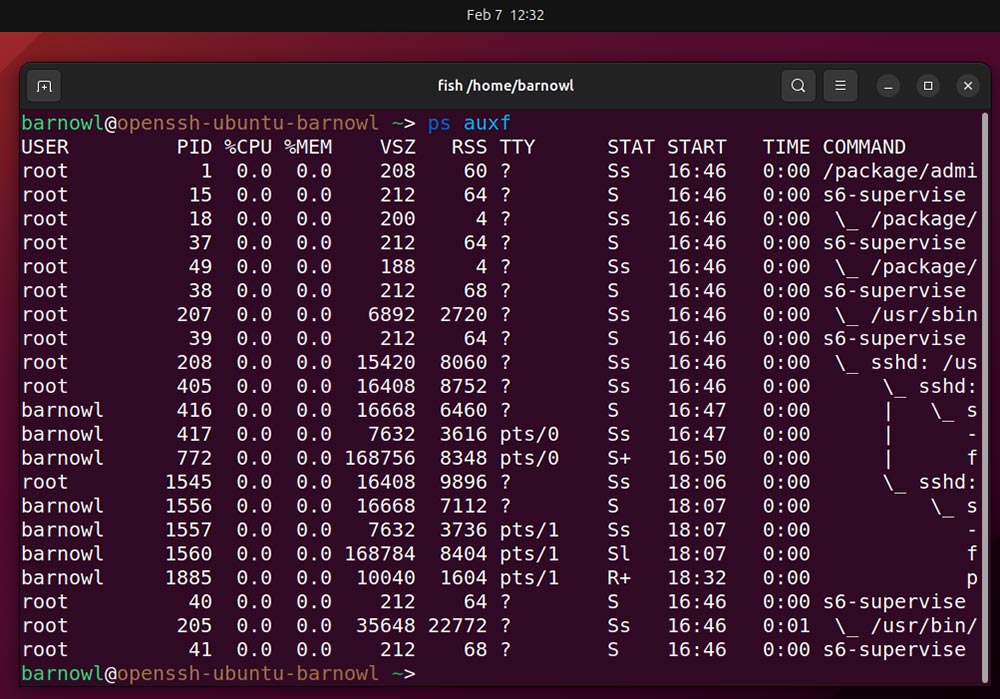
Verify the “Command” column once more fastidiously. In the event you don’t acknowledge any processes, use a search engine and lsof as within the earlier step to establish them. Use Ctrl + C to exit.
Step 6. Verify Community Processes
Expert hackers typically set up backdoor packages configured solely to pay attention for additional directions. These devour minimal CPU/system assets, making them straightforward to overlook.
To be on the protected facet, ensure to listing all processes which are listening for community connections by working:
sudo lsof -i
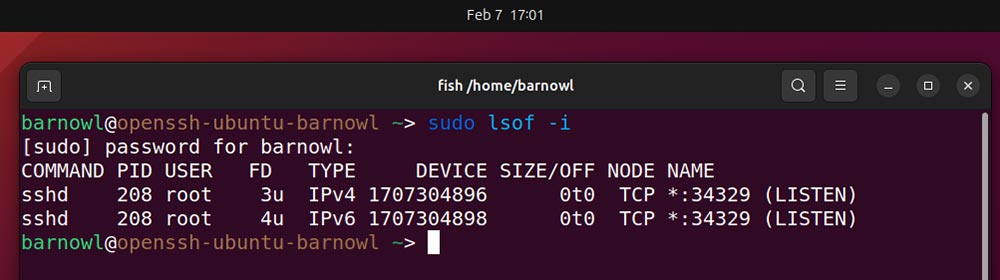
Look towards the tip of every entry to test if the method is in “Hear” mode, i.e., ready for a connection. In the event you don’t acknowledge a course of title, attempt to discover out extra about it utilizing the strategies outlined in Step 4.
Step 7. Terminate Unauthorized Processes
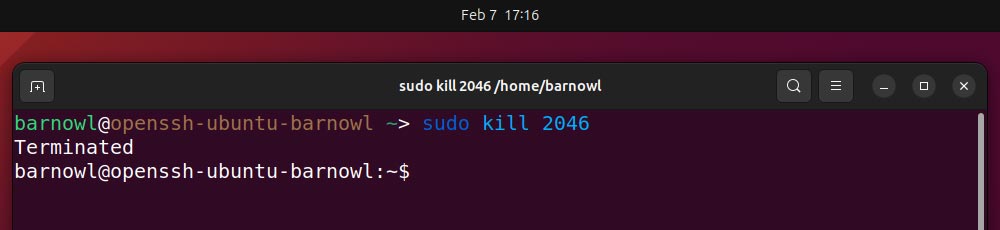
In the event you discover a suspicious course of, you possibly can terminate it instantly utilizing the kill command in addition to the PID:
sudo kill -9 2046
If a program has launched a number of processes, you possibly can terminate all of them with killall:
sudo killall fish
If You’ve Been Hacked
After reviewing logged-in customers, command historical past, and energetic processes you suppose your server is or has been hacked, you possibly can remotely shut it down with the command:
sudo shutdown -h now
In the event you’re renting server house from a 3rd social gathering, you might also be capable of shut it down through the dashboard within the supplier’s net portal. From right here, you possibly can wipe and reinstall the server as you see match.
Seek the advice of Cybersecurity Consultants
Within the occasion that you simply suspect your server has been compromised, particularly if your corporation handles delicate information, it’s paramount to hunt the experience of cybersecurity professionals.
Pc safety consultants can present a complete safety audit, establish the total extent of the breach, and suggest measures to not solely rectify the present vulnerabilities but in addition fortify your defenses in opposition to future assaults.
Bear in mind, the indicators of a hack can typically be delicate, and the implications are far-reaching. Participating with cybersecurity consultants not solely helps in successfully addressing fast safety considerations but in addition in establishing a sturdy framework for safeguarding your digital property in the long run.



Discussion about this post