As we defined in our earlier step-by-step guide, for those who or your supplier have observed uncommon exercise in your Linux server, there are some easy methods to inform in case your knowledge has been compromised.
When you’re positive a hack is going down, it’s time to hold out harm management. On this information, we’ll cowl some primary steps to absorb the wake of a hack, together with isolating your server from the community and making a replica of drives so you possibly can have professionals examine the character and extent of the breach.
You’ll additionally study some finest practices for restoring your server from a clear backup, scanning for malware, imposing new password adjustments, and implementing adjustments to stop future assaults.
Step 1. Isolate the Compromised Server From the Community
Do you have to suspect unauthorized entry or compromise of your Linux server, step one is to isolate it from the community, which can disconnect any unauthorized customers. If malware has contaminated the server, isolating it’ll additionally cease the an infection from spreading throughout the community.
Relying in your location, for those who’re with the server, you possibly can merely disconnect the ethernet cable to do that. Alternatively, for those who’re accessing it through SSH, you should utilize the ifconfig command to disable a selected community interface:
sudo ifconfig <interface_name> down
Make sure to exchange ‘<interface-name>’ with that of the particular interface, e.g., ‘eth0’. To view an inventory of all out there community interfaces, run:
ls /sys/class/web/
In case your server has wi-fi capabilities, you possibly can block all of those connections with:
sudo rfkill block all
Step 2. Create a Snapshot of All Energetic Processes
Documenting and logging each facet of the server is crucial for authorized compliance and for additional investigations to make sure that hacks like these don’t occur once more.
This documentation may very well be precious proof if any rogue or malicious processes are nonetheless working on the compromised server. Save a textual content file of all energetic processes with the command:
ps aux > process_snapshot.txt
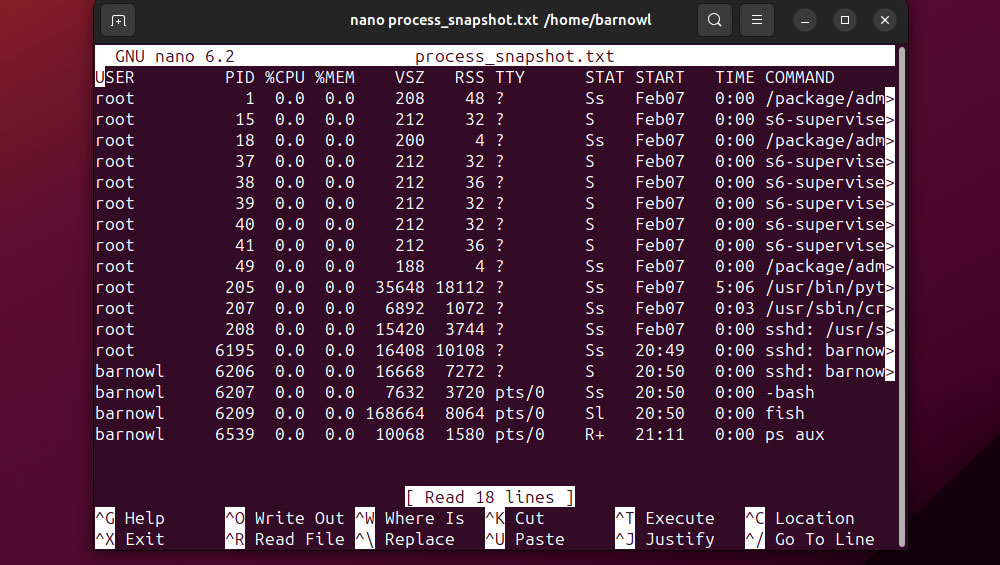
You may view the contents of this file through a textual content editor like GNU nano or Vim.
Step 3. Make a Safe, Offline Backup of All Server Drives
Logging the presently energetic processes is a crucial step in documenting the server hack. Nonetheless, cybersecurity consultants would require a safe picture of your server’s disks to conduct a radical investigation.
The best approach to supply that is to attach a clean, formatted exterior drive to the server. Naturally, this drive must have a capability equal to or (higher but) better than the sum of all of the server drive sizes.
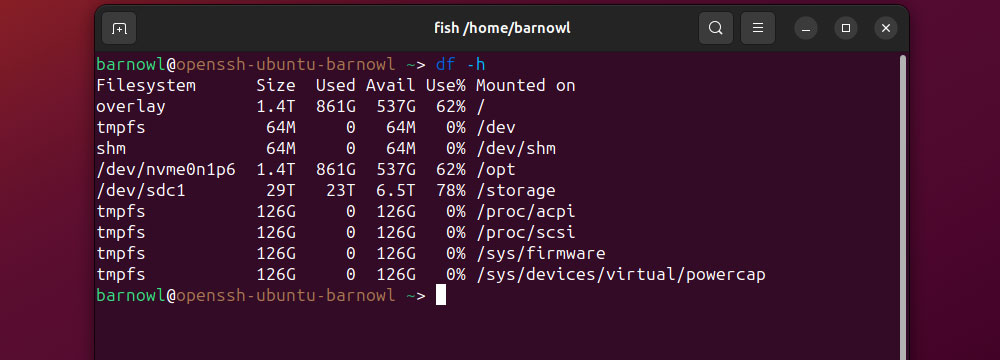
First, have your server listing all drives and used area by opening Terminal and working:
df -h
There are a lot of utilities you should utilize to create copies of the disks. From the command line, ‘dd’ is normally the best. As an example, to repeat the contents of /dev/sdc1 to an exterior drive mounted at /dev/sdb1, run:
sudo dd if=/dev/sdc1 of=/dev/sdb1/server_image.dd bs=4M standing=progress
As soon as the copy course of completes, you possibly can make sure the integrity of the disk picture for later evaluation by producing a cryptographic hash utilizing SHA256 or MD5, e.g.:
md5sum server_image.dd
Be sure to save lots of the hash to the drive, then safely unmount it and retailer it in a protected place.
Step 4. Name within the Cavalry
In case your server has been compromised, search recommendation from cybersecurity professionals. This step turns into particularly essential if the server accommodates info topic to rules just like the GDPR.
Skilled cybersecurity professionals will help you correctly doc the incident and assess the assault vector by analyzing the offline copy of the server drives. This motion will enhance your safety towards an assault the subsequent time it occurs.
Step 5. Restore the Linux Server From a Clear Backup
Offered you’ve been preserving common backups, you possibly can roll your server again to some extent earlier than it was compromised.
This course of is usually a a lot faster technique to recuperate from a breach in comparison with scouring each port, person, and file on the present server for malware or safety flaws.
The precise steps for restoring from a backup will differ primarily based in your server supplier and Linux distro. Nonetheless, you possibly can cut back the prospect of lingering malware by verifying the integrity of your backup and preserving the server remoted from the community through the restoration course of, e.g., by booting the server into Restoration Mode.
In case your chosen OS makes use of the GRUB boot loader, you possibly can restore this together with the working system backup through:
grub-install /dev/sdX
Be sure to exchange ‘/dev/sdX’ with the title of the server’s boot partition. After restoring the backup, proceed to run a full system replace.
Step 6. Scan for Malware
Regardless of your finest efforts to make use of a clear backup, it’s attainable that your Linux server might have been compromised for a while. Due to this fact, the next step ought to all the time be to scan your newly restored Linux server for malware utilizing respected antivirus instruments.
ClamAV stays among the finest malware scanners for Linux servers. For those who don’t already use ClamAV, set up it on Ubuntu Server through:
sudo apt-get set up clamav
Purple Hat customers can set up ClamAV through:
sudo dnf set up clamav
If ClamAV is put in already, make certain to replace the virus definitions database through:
sudo freshclam
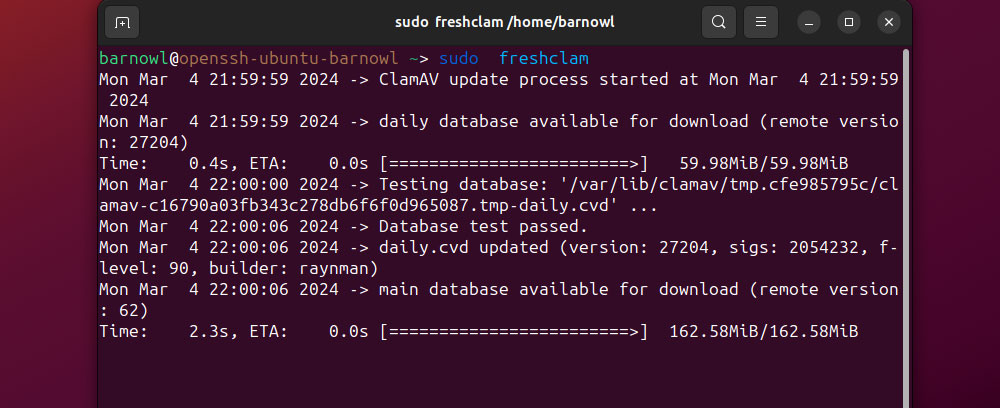
Now you can run a recursive scan for malware and take away any contaminated information:
sudo clamscan -r –take away /
We additionally advisable putting in and working both ‘chkrootkit’ or ‘rkhunter’ to scan for and take away rootkits, as these can reinfect servers which have been restored from a backup.
Step 7. Reset All Credentials
If you restore your server from a backup, this consists of login knowledge like usernames and passwords. If this knowledge has been leaked, nothing can cease a hacker from breaching your system once more.
You may mandate a password reset for particular person accounts utilizing the ‘chage’ command by configuring the -d flag (password expiry time) to 0. To do that for person ‘barnowl’, as an illustration, simply run:
sudo chage -d 0 -M 0 -I -1 -E -1 barnowl
When you’ve got a lot of customers on the server, you should utilize a ‘for’ loop to iterate a compulsory password change for all accounts:
for username in $(reduce -d: -f1 /and so forth/passwd); do
sudo chage -d 0 -M 0 -I -1 -E -1 $username
performed
Be sure additionally to overview present password insurance policies through:
sudo nano /and so forth/safety/pwquality.conf
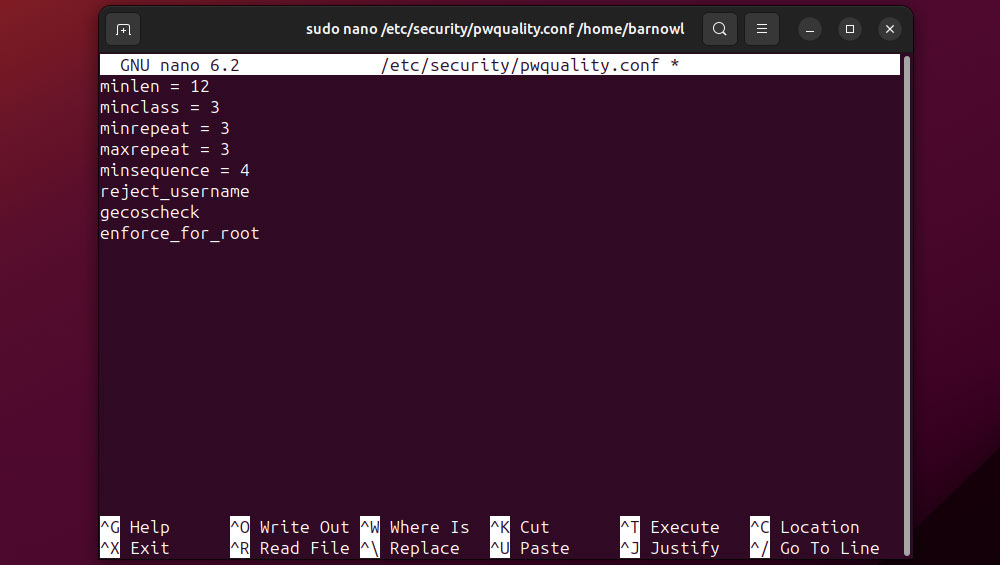
From right here, you possibly can mandate password necessities. For instance, to specify a minimal password size of 12 characters, add:
minlen = 12
Step 8. Armor Up
After your chosen cybersecurity professionals have accomplished their evaluation, you possibly can decide the assault vector used final time your server was compromised. They’ll then advise you on additional steps to safe your server.
As an example, they might advise you to guard the server towards ‘brute power’ password assaults by putting in and configuring ‘fail2ban’ to detect the IP addresses of a number of failed login makes an attempt and block them accordingly.
Cybersecurity consultants may additionally advise you to implement two-factor authentication (2FA) for customers connecting through SSH through frequent packages like libpam-google-authenticator.
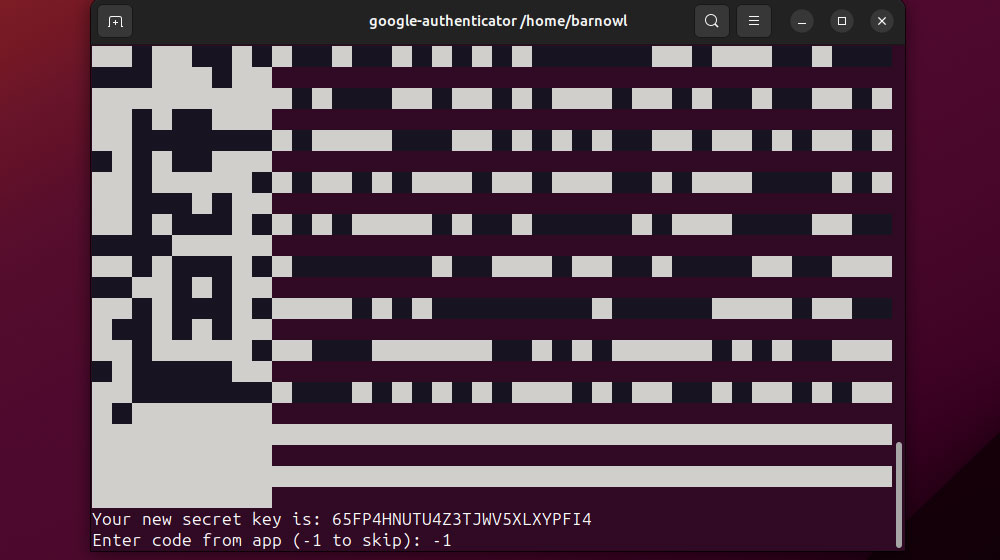
Customers might want to run the software from their very own account initially after which generate codes utilizing a devoted authenticator app.
The server can also want extra safety patches and up to date configuration information. Observe the recommendation of your cybersecurity professionals to the letter.
From Restoration to Resilience
When dealing with the challenges of a compromised server, keep in mind that restoration is just the start. By following these steps, you can’t solely restore your system’s integrity but in addition fortify your defenses towards future threats.
Keep vigilant, hold your safety measures updated, and keep in mind that the cybersecurity panorama is consistently altering. With applicable precautions and companions, you possibly can efficiently safe your Linux server atmosphere.



Discussion about this post