In what may belong within the “higher late than by no means” class, the U.S. authorities and the computing trade are ramping up efforts to take care of seemingly runaway cybersecurity points.
On Friday, the Division of Homeland Safety introduced that its Cyber Security Assessment Board (CSRB) will conduct a assessment on cloud safety involving the malicious focusing on of cloud environments.
The initiative will give attention to offering suggestions for presidency, trade, and cloud providers suppliers (CSPs) to enhance id administration and authentication within the cloud.
Preliminary efforts will assessment final month’s Microsoft cloud hack during which researchers discovered that Chinese language hackers cast authentication tokens utilizing a stolen Azure Energetic Listing enterprise signing key to interrupt into M365 e mail inboxes. The hack led to the theft of emails from roughly 25 organizations.
The board will then develop to points concerned with cloud-based id and authentication infrastructure affecting relevant CSPs and their clients. This a part of the assessment could have much more widespread significance in fixing damaged cybersecurity processes.
US Enhances Cloud Safety Measures
The CSRB’s function is to evaluate vital incidents and ecosystem vulnerabilities and make suggestions primarily based on the teachings realized. In accordance with authorities officers, the board brings collectively one of the best experience from trade and authorities.
“The Board’s findings and suggestions from this evaluation will advance cybersecurity practices throughout cloud environments and make sure that we will collectively preserve belief in these crucial methods,” supplied Cybersecurity and Infrastructure Safety Company (CISA) Director Jen Easterly.
In a associated announcement on Aug. 8, the National Institute of Standards and Technology (NIST) launched a draft of an expanded cybersecurity framework model 1.0 it first launched in 2014. Cybersecurity Framework (CSF) 2.0 is the primary revision of the cybersecurity evaluation instrument since then.
After contemplating greater than a yr’s value of neighborhood suggestions, NIST launched the brand new draft model of the Cybersecurity Framework (CSF) 2.0 to assist organizations perceive, cut back, and talk about cybersecurity threat. It displays adjustments within the cybersecurity panorama and makes it simpler to implement the cybersecurity framework for all organizations.
“With this replace, we try to mirror present utilization of the Cybersecurity Framework and to anticipate future utilization as effectively,” mentioned NIST’s Cherilyn Pascoe, the framework’s lead developer.
“The CSF was developed for crucial infrastructure just like the banking and power industries, however it has proved helpful all over the place, from faculties and small companies to native and overseas governments. We need to be sure that it’s a instrument that’s helpful to all sectors, not simply these designated as crucial,” she added.
Dovetailing Earlier Cyber-Security Methods
The White Home on Thursday opened a request for info for public touch upon open-source software program safety and memory-safe programming languages.
The purpose is to construct on its dedication to spend money on creating safe software program and software program growth strategies. The request for public remark additionally seeks to advance initiative 4.1.2 of the Nationwide Cybersecurity Technique Implementation Plan the White Home launched to safe the inspiration of the web.
The White Home on July 13 issued the Nationwide Cybersecurity Technique Implementation Plan (“NCSIP”). It identifies 65 initiatives led by 18 totally different departments and businesses designed as a roadmap for implementing the U.S. National Cybersecurity Strategy it launched in March.
Responses are due by 5:00 p.m. EDT on October 9, 2023. For info on submitting feedback, see the Fact Sheet: Workplace of the Nationwide Cyber Director Requests Public Touch upon Open-Supply Software program Safety and Reminiscence Protected Programming Language.
Microsoft Response Might Set Precedent
In accordance with Claude Mandy, chief evangelist for information safety at Symmetry Systems, the above-referenced Microsoft cloud breach highlighted two points.
First, it revealed how Microsoft’s industrial constructs bundle wanted security measures with different merchandise. The intent is to limit clients from deciding on aggressive merchandise on a industrial foundation, he mentioned.
That restricts corporations from having important security measures with out paying for greater than what is required. On this case, it entails logs within the authentication course of, based on Mandy.
The second revelation is that particulars on how the breach occurred and what potential affect and information might be impacted are nonetheless obscure, with no certainty offered by Microsoft, Mandy proffered. That occurred regardless of the main target and funding from Microsoft on cybersecurity as a income stream.
“As an trade, we’re demanding extra transparency,” he instructed TechNewsWorld.
Probably the most vital lesson from this breach for organizations, he famous, is that logging and monitoring of knowledge occasions — or information detection and response — is the most important lever that one has within the cloud to detect, examine, and reply to safety incidents, significantly these involving third events.
“Most fascinating within the quick time period from this assessment can be how far the precedent that Microsoft has set in committing to offer these logs at zero value can be adopted or enforced upon different cloud service suppliers,” he mentioned.
Half of Cloud Safety Faults Ignored
The Qualys Menace Analysis Unit analyzed the state of cloud safety and launched findings earlier this month.
Researchers found that misconfigurations in cloud safety suppliers offered ample alternatives for risk actors to focus on organizations, particularly when mixed with externally dealing with vulnerabilities that remained uncovered and put organizations in danger, based on Travis Smith, VP – Menace Analysis Unit at Qualys.
“Throughout the three main cloud safety suppliers, configuration settings designed to harden cloud architectures and workloads had been solely enabled accurately roughly 50% of the time. On an identical word, 50.85% of externally dealing with vulnerabilities stay unpatched,” he instructed TechNewsWorld.
Whereas a assessment will present visibility into the dangers of transferring computing assets to the cloud, it doesn’t seem that organizations are heeding that warning, Smith confided.
That discovering doesn’t bode effectively for higher cybersecurity. The researchers’ first assessment targeted on vulnerabilities in Log4J. Cyber specialists are seeing that Log4Shell remains to be broadly prevalent in cloud environments, with patches discovered 30% of the time, he supplied.
No Answer for Key-Based mostly Cloud Safety
Key-based safety will at all times have this breaching drawback. There may be at all times, in some sense, a grasp key, one key to rule all of them, instructed Krishna Vishnubhotla, VP of product technique at Zimperium. So simply selecting strong cryptographic algorithms and schemes isn’t sufficient.
“The extra vital concern is defending the keys from being exfiltrated and abused. Preserving keys safe isn’t a sound apply in most enterprises,” he instructed TechNewsWorld.
Multicloud and hybrid cloud are pervasive all through the enterprise, from computing to authentication. Due to this fact, the grasp key represents entry to all enterprise methods.
“Whether or not enterprises ought to entrust their grasp keys to Cloud Suppliers or if the enterprises ought to tackle this duty is the actual query,” he instructed.
New Cybersecurity Framework Holds Promise
Efforts to replace safety suggestions might be an uphill battle past precise cyber specialists. One of many perennial issues in cybersecurity is tips on how to discuss safety to management and the board quantitatively, supplied John Bambenek, principal risk hunter at Netenrich.
“Increasing these frameworks to all organizations and never simply crucial infrastructure opens the door to having the ability to take action in a constant method throughout the economic system and hopefully will result in extra buy-in of utilizing safety to scale back enterprise threat,” he instructed TechNewsWorld.
The addition of a sixth perform, “govern,” is a transparent message to organizations that to achieve success, there additionally should be actively managed insurance policies and processes underpinning the opposite practical areas, praised Viakoo CEO Bud Broomhead.
For instance, governance ought to make sure that all methods are seen and operational and that enterprise-level safety processes and insurance policies are in place.
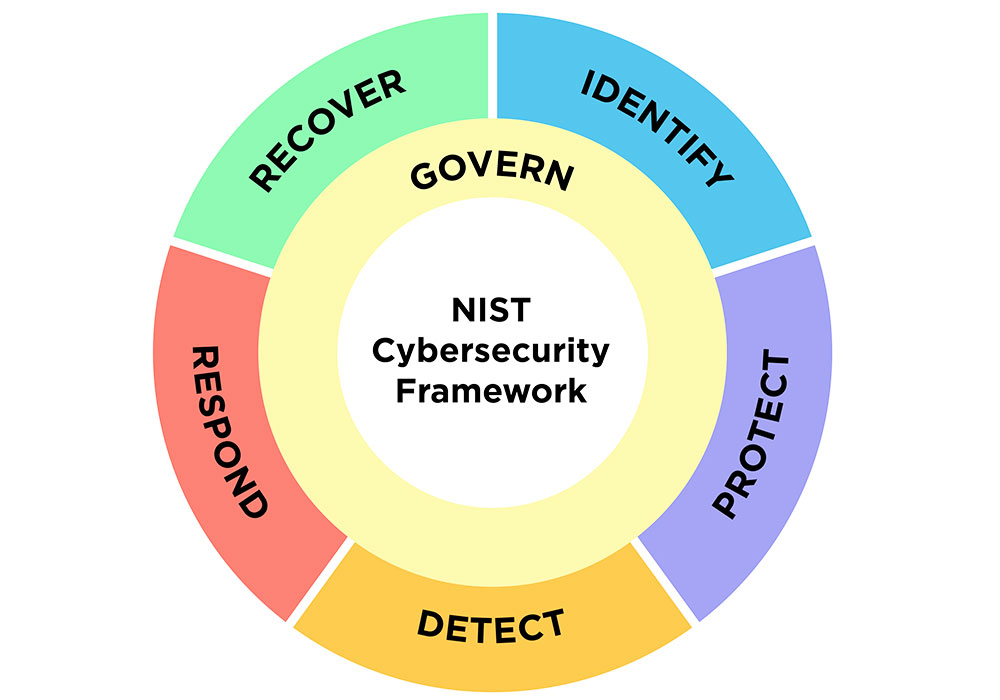
To the 5 major pillars of a profitable cybersecurity program, NIST has added a sixth, the “govern” perform, which emphasizes that cybersecurity is a serious supply of enterprise threat and a consideration for senior management. (Credit score: N. Hanacek/NIST)
Increasing the scope of the NIST framework to all types of organizations, not simply crucial infrastructure, acknowledges how each group faces cyber threats and must have a plan in place for managing cyber hygiene and incident response, Broomhead defined.
“That is already the case with cyber insurance coverage, and NIST’s latest replace will assist organizations not simply cut back their risk panorama but in addition be higher positioned for compliance, audit, and insurance coverage necessities on cybersecurity,” he instructed TechNewsWorld.
Step within the Proper Route
NIST’s replace also needs to push extra organizations to work with managed service suppliers on their cyber hygiene and cybersecurity governance, Broomhead urged.
Provided that NIST expands its scope to incorporate smaller organizations, many will discover {that a} managed service supplier is one of the best ways to make their group compliant with the NIST Cybersecurity Framework v2.0.
The newest replace to the Cybersecurity Framework is a superb refresh of among the best cybersecurity threat frameworks, supplied Joseph Carson, chief safety scientist and advisory CISO at Delinea.
“It’s nice to see the framework transferring on from merely a spotlight of crucial infrastructure organizations and adapting to cybersecurity threats by offering steerage to all sectors,” he instructed TechNewsWorld.
“This consists of the brand new govern pillar acknowledging the adjustments in the best way organizations now reply to threats to assist their general cybersecurity technique.”




Discussion about this post